
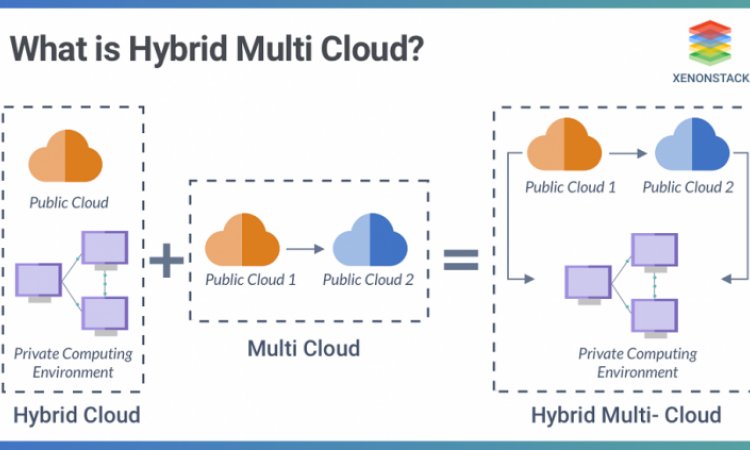
How to protect yourself in a multi cloud environment?
As companies expect to be more agile and flexible while
saving money by moving their workloads to the cloud, the trend towards
multi cloud is gaining ground. Initially, 86% of IT administrators already use
multiple clouds. While the vast majority of the rest plan to adopt it in the
next few years. Either way, security remains a major challenge in this
decision. It is still possible to find a solution based on best practices
related to improving security in the cloud age.
Ensure safety at the workload level
Separating cloud-stored workloads from underlying hardware
is a fundamental change in protection. This is because containers and virtual
machines can move freely between on-premises infrastructures and the public
network. Specifically, workloads share physical hosts and internal network
resources with unknown third parties. Therefore, this phenomenon constitutes a
real danger for the notion of network perimeter.
To guarantee security in this type of architecture, it is
essential to protect the equipment. Protection measures must be defined at the
software level, among others, application firewalls and intrusion prevention
systems. They must also be registered at the workload, container, or virtual
machine level. Other than that, ensuring data protection regardless of
operating system requires decoupling security from hardware and workloads.
Play in the balance between control and cyber hygiene
In cyber security, the balance between security and ease of
use is well known. There are, for example, the blocking of TCP ports, the
blocking of the image of the workstation or the denial of administrator rights
to users that allow to avoid actions that could compromise security. You should
know that these static measurements cannot be adapted to the multi cloud era. In
addition to interfering with the user experience, they are insufficient against
possible threats since the environment is more complex. Therefore, it is
important to find a complex compromise such as a cyber-hygiene-focused
approach. This is aimed at continuously monitoring and evaluating all
technology services and the IT environment.
Conduct an internal audit from the start
The notion of multi-vendor controlled infrastructure is
sometimes incompatible with the control efforts of a company's IT department.
However, during internal audits, it is critical that a company justifies
compliance of external vendor operations with requirements as well as internal
security standards. Therefore, this obstacle can damage the reputation of the
department, but especially IT security. Therefore, it is important to conduct
an internal audit in advance to define the selection and design process. This
decision can prevent all kinds of problems in the future.




